Of late, media has been abuzz with the talk of GPS spoofing—basically whipping up a doomsday scenario where terrorists would spoof the GPS, unleashing total chaos making passenger jets crash or test fired missiles go haywire and start unintended wars. The Hindu, for example, carried an article with the title ‘Airlines report ‘severe’ GPS spoofing over Delhi for 7 days’.
This is all plain and simple unadulterated bullshit. People writing in the mainstream media do not have the faintest idea of how exactly GPS functions, not to speak of what spoofing is and whether it is feasible. Before I debunk the myth summarily, we must know how exactly this weird idea got hold of popular imagination?
‘Tomorrow Never Dies’, the Original Culprit of this Scary Idea

In the 1997 James Bond film ‘Tomorrow Never Dies’, the central villain, media tycoon Elliot Carver, hatches a diabolical plan to ignite a war between the United Kingdom and China. His ultimate goal? To create global chaos that positions his media empire, the Carver Media Group Network, as the sole source of wartime news, securing him exclusive broadcasting rights in China for the next century. To pull this off, Carver pins his hopes on GPS spoofing and a stolen encoder to serve as the spark.
Carver’s cyber-terrorist associate, Henry Gupta, snags a cutting-edge GPS encoder from a rogue dealer. In the film, the device is capable of intercepting, altering, and retransmitting GPS signals. By hijacking the satellite-based Global Positioning System that ships, planes, and missiles depend on for navigation, the encoder can invisibly reroute entire vessels without anyone on board realizing they’re off course. Carver deploys this tech against the British Royal Navy frigate HMS Devonshire, which is conducting routine patrols in the South China Sea. Devonshire blunders into Chinese territorial waters. Carver destroys it there by a torpedo and his media outlets blame it on Chinese aggression.
As the world totters on the brink of a nuclear war, it is only Bond who can destroy the encoder and save the world. All hail 007 who, like before, does not fail this time too.
How GPS/GNSS Positioning actually works

Global Navigation Satellite Systems (GNSS) include constellations of Earth-orbiting satellites that broadcast their locations in space and time, of networks of ground control stations, and of receivers that calculate their own ground positions from that by trilateration.
At present GNSS include two fully operational global systems, the United States’ Global Positioning System (GPS) and the Russian Federation’s GLObal NAvigation Satellite System (GLONASS), as well as the developing global and regional systems, namely Europe’s European Satellite Navigation System (GALILEO) and China’s COMPASS/Bei-Dou, India’s Regional Navigation Satellite System (IRNSS) and Japan’s Quasi-Zenith Satellite System (QZSS).
The Physical Layer: Satellites, Carriers, Codes
GNSS satellites (GPS, Galileo, GLONASS, BeiDou) continuously broadcast carrier waves at microwave frequencies (GPS L1 = 1575.42 MHz is the familiar one). Each satellite transmits a spreading code (pseudorandom sequence), plus a navigation message containing satellite clock and orbit (ephemeris) data. The receiver locks to the carrier and correlates with the code to identify the satellite and extract timing/navigation data. modern receivers often use multiple constellations and frequencies for robustness.
Ranging and trilateration (why timing is everything)
Each satellite transmits the time-of-transmission. A receiver measures the time delay between when the satellite transmitted and when it received the signal; since signals travel at the speed of light, that delay × c is the pseudorange (satellite → receiver).
By receiving signals from (at least) four satellites, a receiver solves for four unknowns: x, y, z (position) and the receiver clock bias (the receiver’s clock is not an atomic clock). This is the core of GNSS positioning. Any error in clock, ephemeris, or measured delay produces position error.
Important observables beyond “position”
Receivers do much more than spit out a lat/long — they also monitor:
- Carrier-to-noise density (C/N0) per satellite (signal strength/quality);
- Doppler shifts (satellite relative velocity produces a predictable Doppler trace);
- Code-phase and carrier phase (for high-precision users);
- Navigation message contents (satellite clock and orbit almanac/ephemeris);
- Signal timing consistency across satellites (geometry, residuals).
These are exactly the things a good spoof-detection algorithm inspects.
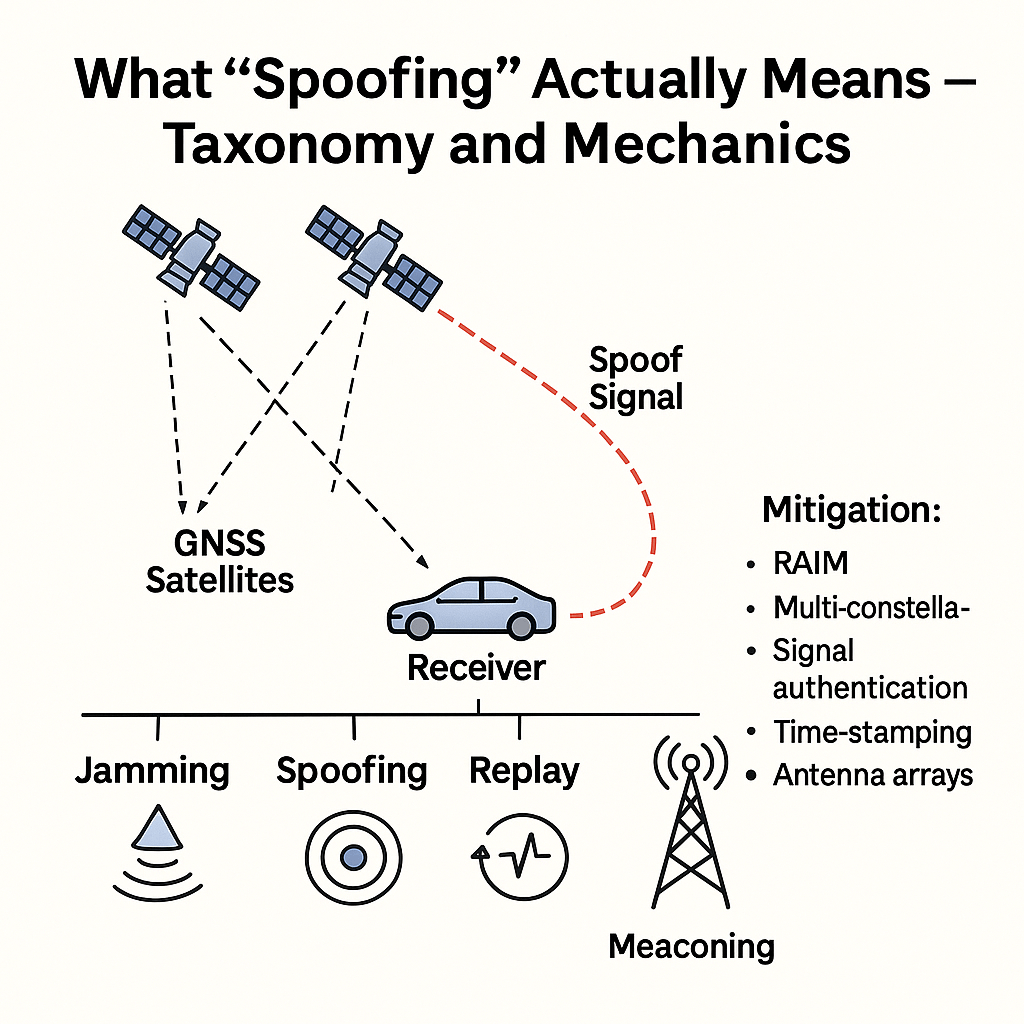
“Spoofing” is not one single attack — there are distinct classes with very different technical requirements.
Basic types
- Meaconing — simple replay of genuine signals (capture and rebroadcast with delay). Easy conceptually but creates time offsets and is often detectable.
- Simple spoofing (single-satellite or inconsistent spoof) — broadcasting false signals that don’t match genuine satellites; can confuse cheap receivers in close proximity if attacker overpowers satellites. Easier to detect on robust receivers.
- Seamless takeover / coherent multi-satellite spoofing — attacker first transmits counterfeit signals at lower power to “lock” a receiver, then gradually increases power and carefully controls code phase, carrier phase, Doppler, and navigation data for multiple satellites to move the victim’s computed position/time without triggering alarms. This is the hardest and most sophisticated form — but it’s also what research teams demonstrated in controlled tests.
Why Coherent, Multi-Satellite Control is required
Because a receiver computes position by combining many satellite pseudoranges, an attacker who fakes only one satellite’s signal will produce inconsistent position/time residuals that modern receivers and cross-checks (Receiver Autonomous Integrity Monitoring-RAIM, sensor fusion) will flag. To move a receiver’s computed location plausibly, the attacker must present a self-consistent set of signals that mimic many satellites at once (correct relative timing, Doppler, and navigation messages). That multiplies the attacker’s difficulty.
The Technical Obstacles an Attacker Faces
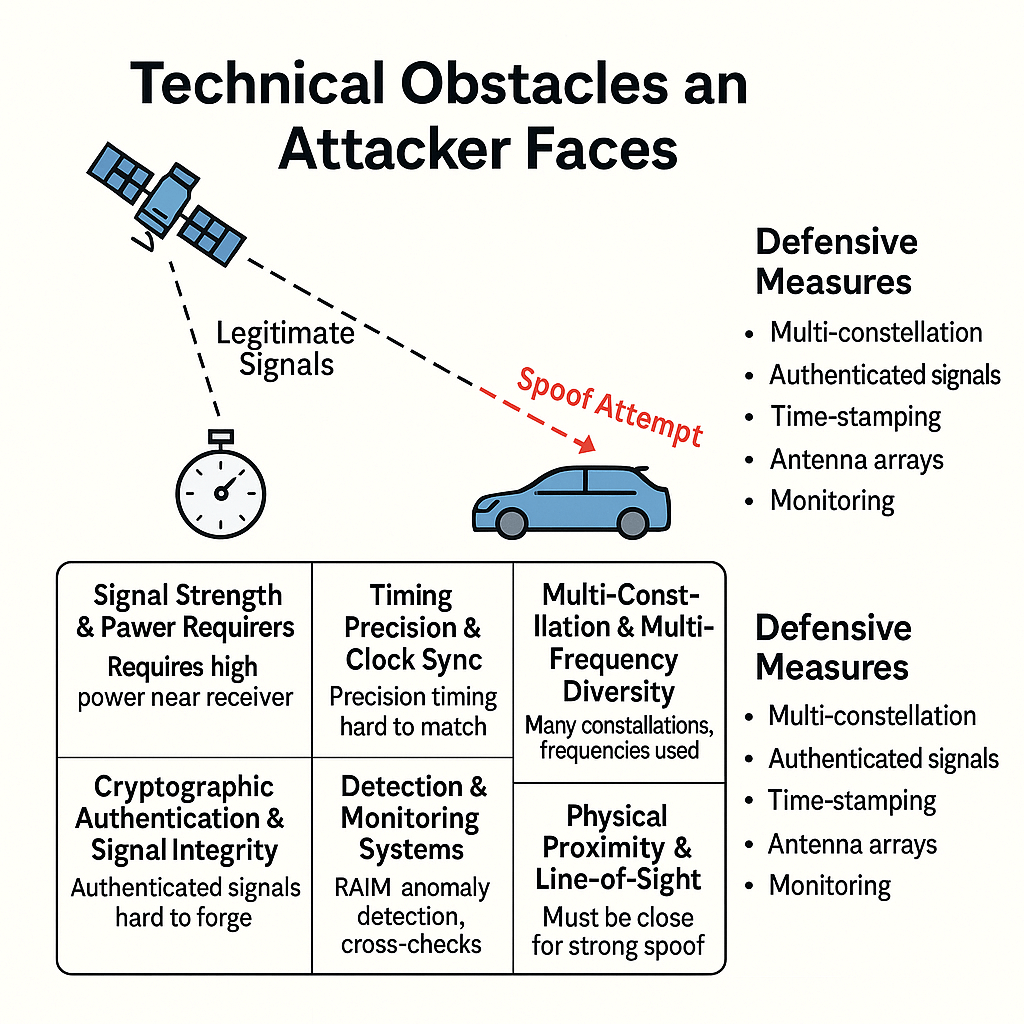
Below I list concrete, measurable difficulties—these explain why spoofing is not a 5-minute job or the job of a bunch of terrorists operating from some basement—the favourite nightmare of the journalists.
Power and Line-of-Sight (LOS)
GNSS satellite signals received at the ground are extremely weak (signal levels are often around −130 dBm or so at the receiver). To override a satellite’s signal at a victim receiver you must transmit a stronger signal at the victim’s antenna than the satellite signal — typically meaning you need a powerful transmitter located relatively close to the aircraft and with correct antenna directivity. That often requires being physically near the aircraft (or to the ground antenna for surface receivers). High-power transmissions also risk detection and interference visibility.
Precise Timing and Code-Phase Control
Receivers correlate incoming waveforms with specific code offsets and carrier phases. To substitute your counterfeit signal without the receiver noticing, you must match code-phase and carrier-phase tightly and then slowly diverge in a controlled way. This is not a “send a wrong lat/long” text message — it requires RF coherent generation with precise timing control, often to the nanosecond level. Seamless takeover demonstrations achieved this, but they used specialized equipment and careful control.
Multi-Satellite Consistency (Ephemeris/Navigation Data)
The attacker must broadcast navigation messages consistent with real satellite ephemerides, clock offsets, and the geometric relationships among satellites. Any mismatch shows up in receiver residuals (bad geometry, inconsistent Doppler). Creating a convincing constellation of counterfeit satellites is far harder than spoofing a single visible satellite.
Doppler/Time Dynamics
Satellite Doppler shifts follow very predictable trends as satellites move in orbit and the platform (aircraft) moves. Spoof signals must reproduce plausible Doppler traces; otherwise receivers — which often use Doppler tracking — notice anomalies. Attacker must predict or measure the victim’s motion and emulate Doppler. That’s a dynamic control problem, not a static one.
Antenna / Angle-of-Arrival Defences in Aircrafts
Many professional/aviation receivers and installations use multi-antenna systems or directional coupling that can detect impossible angles of arrival (all signals coming from the same direction) — a classic sign of a ground-based spoofer. For airborne systems where only a single antenna is used, angle-of-arrival is harder to test, but integrated systems mixing INS data provide crosscheck.
Integration with Inertial and Navigation Sensors of Aircrafts
Modern airliners have Inertial Reference Systems (IRS/INS) and multiple sensors (air data, ground speed from radar/ADS-B) that provide independent motion/attitude estimates. Sudden unexplained position/velocity jumps that contradict inertial/sensor fusion logic are suspicious and can be detected. High-integrity flight systems and human crosschecks reduce the chance a spoofer can stealthily change an aircraft’s path.
Multi-Constellation and Multi-Frequency Receivers
Receivers that simultaneously use GPS, Galileo, BeiDou, GLONASS, and multiple frequencies (L1/L2/L5/E1/E6 etc.) require an attacker to spoof all those signals coherently or else face cross-constellation inconsistencies. That greatly raises the attacker’s required power/complexity.
Why Airliners Cannot Just Be Made To Go Astray and Crash

- Operational logistic and proximity constraints. To spoof an in-flight aircraft’s GPS well enough to control it, you need to be close, under the aircraft, or have a high-power transmitter aerial solution. That increases risk for the attacker and makes remote, clandestine spoofing at cruising altitudes much harder. The demonstrated successful real-world spoofing incidents have been localized (ports, taxis, near-shore zones) where ground-based transmitters were present.
- Defence-in-Depth in Aviation. Airliners do not rely on GPS alone for ultimate flight control; there are pilot inputs, INS, navigation aids (VHF omnidirectional range (VOR) and a distance-measuring equipment (DME), ILS for approaches), ATC surveillance (radar/ADS-B), and human monitoring. Even if GPS-derived position drifted, pilots and systems would notice cross-check inconsistencies. Overriding all of these in a stealthy way requires a far more complex attack than demonstrating brief position errors on a single consumer GPS.
- High skill and custom equipment required. The few ublic demonstrations in the past used expensive, custom hardware and signal-generation expertise; they were explicitly research tests, often performed with the consent of the target or in controlled conditions. That is far from a low-cost, widely-deployable “terrorist weapon.”
So while possible in lab or with clever local setups, widespread, stealthy, high-confidence spoofing of commercial airliners in normal operations is not trivial and certainly not a practicable or feasible option for terror groups compared with other means.
Real Demos and Incidents — What They Showed and What They Did Not
- Cornell / Virginia Tech / UT Demonstrations (2008–2013 et seq.) — researchers demonstrated that receivers can be spoofed: from small drones to an $80M yacht at sea (UT Austin team led by Todd Humphreys). Those experiments were landmark proof-of-concept and deliberately crafted to show vulnerabilities and encourage countermeasure development. They required expertise and custom equipment; they also uncovered the pathway to mitigation.
- Sea/Port Region Interference/Spoofing Reports (e.g., Black Sea, Russian Coastal Examples) — there are documented real-world reports where many ships’ reported positions were odd or displaced; investigations indicate localized interference/spoofing in certain politically sensitive areas. These events display that spoofing can be used opportunistically to cause confusion, especially for less-sophisticated receivers (taxis, phones, small vessels), but they are not stealthy worldwide attacks on airliners.
- Aviation Industry Reporting — aviation-focused industry groups have documented increasing GPS interference events in recent years; many are jamming (loud interference) rather than subtle coherent spoofing, and several incidents were due to ground-based sources (intentional or accidental). Aviation groups stress logging and forensic analysis of receiver raw data before claiming ‘spoofing.’
Key takeaway: Researchers proved that spoofing is technically possible; operational experience shows interference events occur and can disrupt positioning. But the leap from “there were odd GNSS readings” to “this was a coordinated terrorist sabotage of airliners” requires much stronger evidence (raw receiver IF/IQ logs, multi-receiver correlation, spectrograms, or physically located transmitters).
Detection and Mitigation—Why Modern Systems Are Resilient and Getting Better
A layered approach reduces risk:
Receiver-level checks
- C/N0 monitoring (unexpected large changes in signal strength are a red flag).
- Doppler / carrier-phase consistency checks (spoofed signals that do not match expected Doppler/phase trends will be suspicious).
- RAIM (Receiver Autonomous Integrity Monitoring) / multi-constellation cross-checks identify inconsistent pseudoranges. Civil aviation uses these methods for integrity.
System-Level and Cryptographic Protections
- Galileo OSNMA (Open Service Navigation Message Authentication) provides data-message authentication so receivers can verify navigation messages as genuinely from Galileo; OSNMA has moved to operational status in 2025. This raises the bar against spoofers who try to falsify navigation messages.
- GPS civilian authentication (Chimera, etc.) — proposals and prototypes (Chimera / other schemes) aim to add robust cryptographic authentication for GPS L1C and other signals. These are in development and expected to further reduce spoofing feasibility as receivers adopt them.
Multi-Sensor Fusion
INS/Gyro/Air-data/ADS-B/Secondary Surveillance provide independent motion and position estimates; sudden uncorrelated deviations between GNSS and INS are a classic detection mechanism. Aviation safety systems and pilot practice rely on crosschecks.
Policy and Monitoring
Spectrum monitoring and geolocation of interference sources: high-power spoofers/jammers create RF signatures traceable by monitoring networks and regulators (NIST/CISA guidance on PNT resilience).
What Journalists fail to understand in their Ignorance?
Because most journalists are practically illiterates in matters of high technology like this, they fail to understand that if there is a claim of GPS of aircrafts having been “spoofed,” they must necessarily be supported by the following technical data points before jumping to the sensational:
- Raw receiver observables: per-satellite C/N0, Doppler histories, pseudorange residuals, and time-of-week offsets. (These are available in many avionics/flight data logs.)
- IF/IQ recordings or spectrograms that show the actual RF environment (presence of anomalous high-power signals, spectral occupancy).
- Correlation across receivers/ground stations: did other aircraft or ground GNSS monitors see the same anomalies at the same time/location? Wide-area correlation points to systemic spoofing; single-aircraft anomalies could be equipment faults.
- Physical source search: localization attempts for any ground transmitter suspected of spoofing.
- Cross-checks with independent sensors (INS, radar tracks, ADS-B, ATC observations). If those contradict GNSS outputs, that’s evidence of GNSS fault/attack.
Without this chain of evidence, labelling an episode “severe spoofing” is not just premature but plainly stupid.
Practical Recommendations for Investigators
- For investigators / regulators: demand raw receiver logs and IF/IQ recordings; do multi-station correlation; publish forensic analyses before declaring causes public. Use the standard GNSS forensic checklist (C/N0, Doppler, pseudorange residuals, raw spectrograms).
- For airlines & avionics designers: continue adoption of multi-constellation and multi-frequency receivers, OSNMA-capable receivers where possible, robust RAIM and sensor-fusion logic, and spectrum monitoring.
Have Some Brains: Why the Terrorists Have Not Been Able To Do It
GPS/GNSS spoofing has been demonstrated in research; the concerns arising from it have been addressed (protocol/authentication, multi-constellation, receiver-side detection). However, practical, covert spoofing sufficient to commandeer a modern commercial airliner in cruise demands a very high level of RF sophistication, proximity or powerful transmitters, and careful multi-signal coherence — not something credibly achievable by a casual non-state actor or terrorist without detection. Therefore, sensational press claims of “airliners steered by spoofers” must be dumped in trash until concrete forensic evidence (receiver logs, spectrograms, multi-station correlation) is shown.
Had it been not so difficult to spoof GPS (or, conversely, so easy to spoof GPS) resourceful terrorist groups of the world like Hamas, Houthis, ISIS, and Al Qaeda would have been sending every single airliner of the world to a watery grave in the oceans by misleading their GPS or making them crash disastrously like 9/11.
In fact, it would have been a most potent weapon of the terrorists.
The very fact that they have not been doing it means that they are not able to do it. For that matter, even the ISI of Pakistan, being extremely resourceful, could have done it and given the equipment to terrorists they sponsor. But, they too have not been able to do it. End of argument!

